Using a gMSA (or sMSA) Account for the MS SQL Server Database Connection to the Application Server
NOT AVAILABLE IN SAAS
If required, a gMSA/sMSA account can be used for the connection between the MS SQL Server database and the Syteca Application Server (e.g. for security reasons).
The instructions in this guide describe how to set up and configure a gMSA/sMSA account (after installing Syteca Application Server) to use for the connection between the MS SQL database and the Syteca Application Server.
NOTE: For the purposes of this guide, both the terms and gMSA (Group Managed Service Account) and sMSA (Standalone Managed Service Account) are further referred to together simply as "gMSA account".
Table of Contents
1. Setting Up a gMSA Account
1.1. Creating a KDS key
a) Add a KDS key, that will be used to generate and store the gMSA passwords (where the password rotates) by running the following command:
Add-KdsRootKey –EffectiveTime ((get-date).addhours(-10)) |
b) Check that the key is added by running the following command (where the expected result is True):
Test-KdsRootKey -KeyId (Get-KdsRootKey).KeyId |
1.2. Creating a gMSA account
a) Run the following commands using PowerShell, that will enable gMSA support:
Install-WindowsFeature RSAT-AD-PowerShell Import-Module ActiveDirectory |
b) Create an Active Directory group, and add the target computers to it, that the gMSA account will be used on.
For example, gmsaServers will be used as an argument to the PrincipalsAllowedToRetrieveManagedPassword parameter in the gMSA account creation command, as follows:
New-ADServiceAccount <gmsa_login> -DNSHostName <FQDN_server> -PrincipalsAllowedToRetrieveManagedPassword <AD_group> -KerberosEncryptionType AES128, AES256 For example: New-ADServiceAccount MyGmsa -DNSHostName "MyGmsa.my.test" -PrincipalsAllowedToRetrieveManagedPassword "gmsaservers" -KerberosEncryptionType AES128, AES256 |
NOTE: The “-KerberosEncryptionType” parameter is optional, but it is recommended to specify explicitly in order to avoid any possible future issues with Kerberos authentication.
c) After creating the gMSA account, reboot the computers that were added to the gmsaServers Active Directory group.
1.3. Installing the gMSA Account
To use the gMSA account on the target computers, do the following:
a) Run the following command (to install the required modules for PowerShell):
Install-WindowsFeature RSAT-AD-PowerShell |
b) Run the following command to install the gMSA account:
Install-ADServiceAccount <gmsa_login> For example: Install-ADServiceAccount MyGmsa |
c) Check that the gMSA account has been installed by running the following command (where the expected result is True):
Test-ADServiceAccount -Identity <gmsa_login> For example: Test-ADServiceAccount -Identity MyGmsa |
d) Repeat the steps above on all the computers that the gMSA account will be used on.
1.4. Granting gMSA Permissions to a “Log on as a Service” Account
a) Open the Local Security Policy by using msc, and then open Local Policies > User Rights Assignment, and for the Log on as a service policy, add the gMSA account.
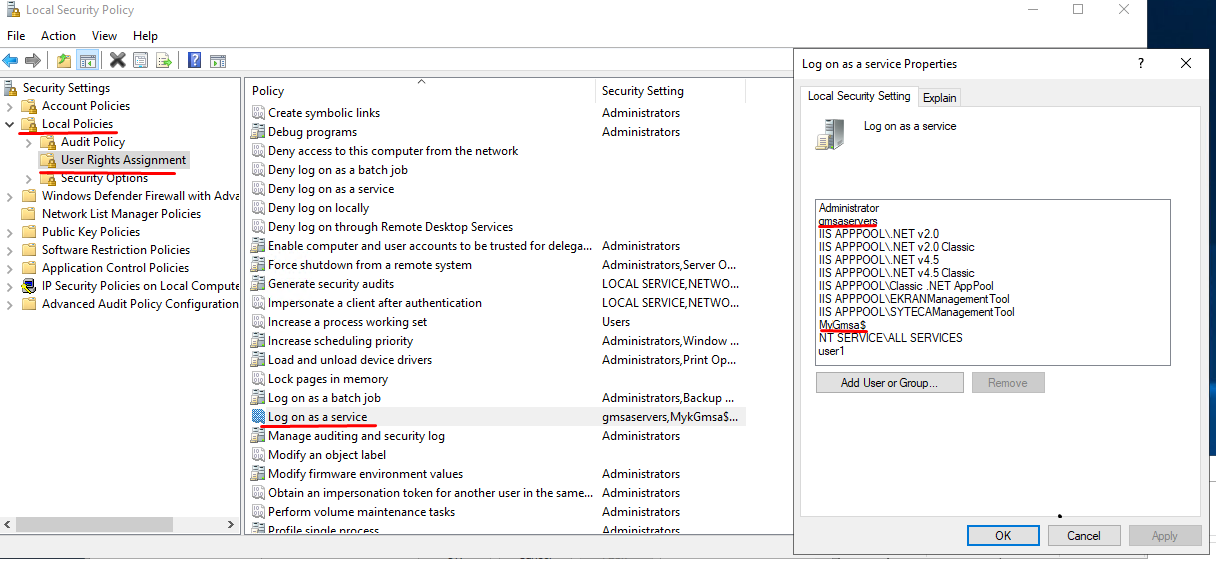
b) Repeat the steps above on all the computers where the gMSA account will be used.
1.5. Granting Permissions to Access System Productivity Counters
a) To prevent an issue with displaying dashboards on the System Health page, and the following “Access to the registry key 'Global' is denied.” error occurring, in the Application Server logs, grant Full Control permissions for the gMSA account in the registry to the Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Perflib folder.
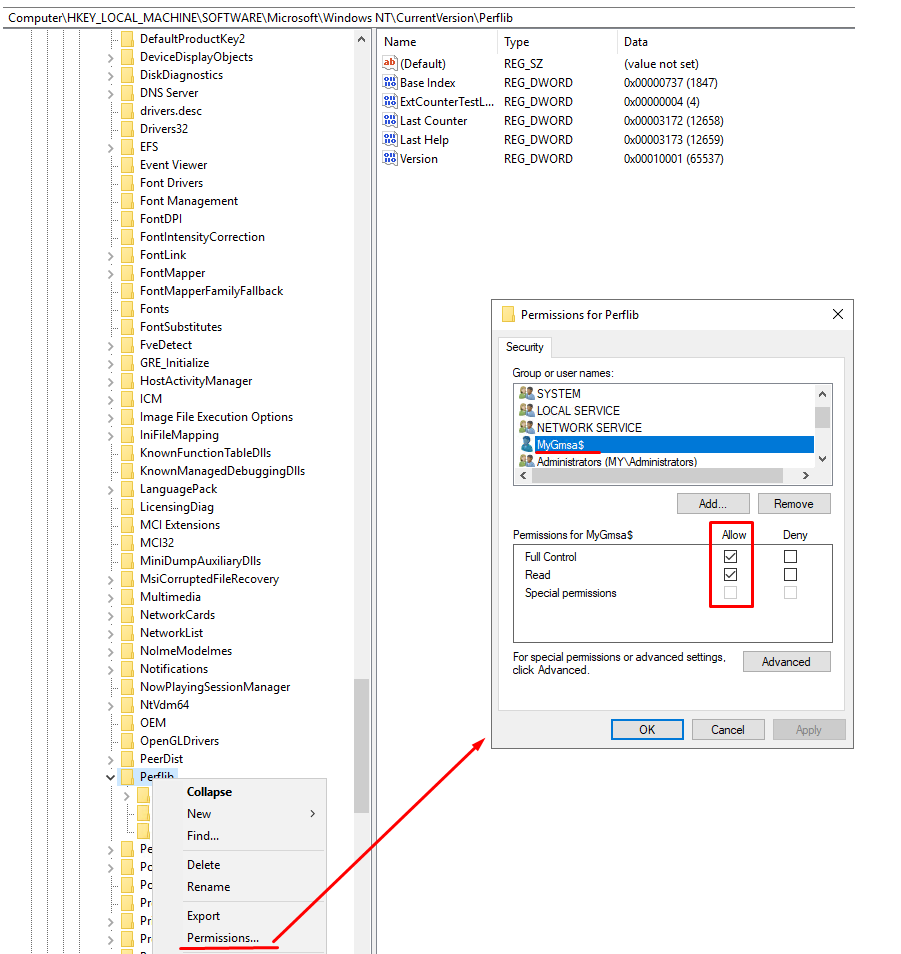
b) For the EkranServer service to be able to start, grant Full control permissions for the gMSA account to the Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\EventLog folder.

1.6. Granting Permissions for the gMSA Account to the Ekran System Folder
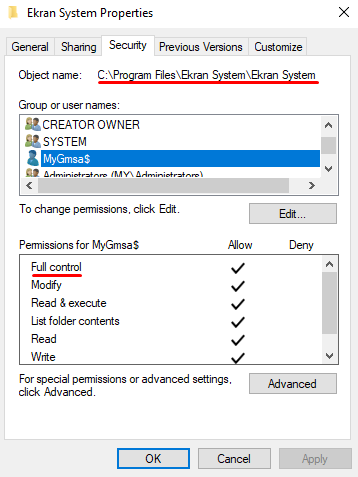
For the information to be written to the Application Server logs, grant Full control permissions for the gMSA account to the C:\Program Files\Ekran System\Ekran System folder.
2. Configuring the Management Tool
2.1. The LDAP Target
To update/add an LDAP target using the gMSA account, do the following:
a) Run the EkranServer service under the gMSA account (e.g. in Windows Services).
b) On the Configuration page in Management Tool, select the LDAP Targets tab, and update/add the required automatic LDAP target manually by clicking the Refresh Automatic LDAP Target button.
2.2. The Database and Archive Parameters
NOTE: The gMSA account needs to be added to the list of users on the "Logins" tab in SQL Server Management Studio, and the "db_owner" permission needs to be granted to it.
To be able to use the gMSA account, configure the database (and archive parameters), as follows:
a) Run the EkranServer service under the gMSA account (e.g. in Windows Services).
b) Restart the SQL Server service under the gMSA account (e.g. in Windows Services).
c) Edit the database parameters defined during installation of the Syteca Application Server by opening the Database Parameters (DbSetupToolUI) application (by right-clicking the Syteca Server icon in the Windows Notification area, and selecting the Database Parameters option), and then select the Windows Authentication option and the Use process credentials checkbox (on the Metadata Storage sub-tab that opens).
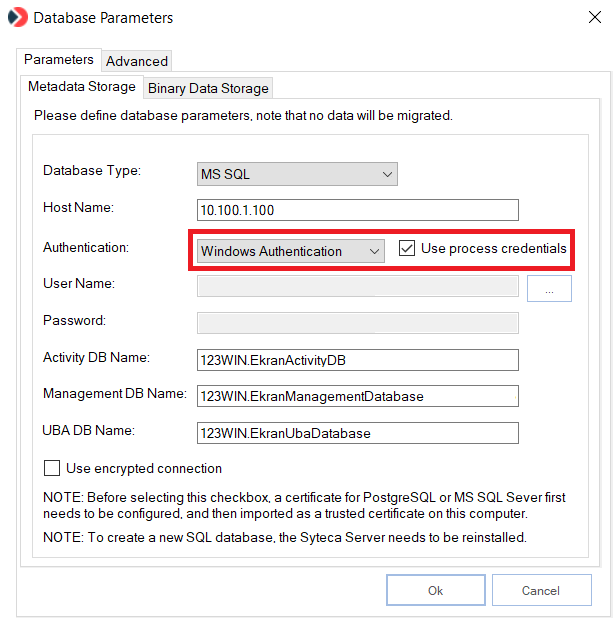
NOTE: The User Name and Password fields are disabled (since the credentials for the gMSA account will be used automatically if it is correctly configured).
d) Also, when configuring the archive parameters, enter any values in the User and Password fields when:
- Defining database archive parameters:
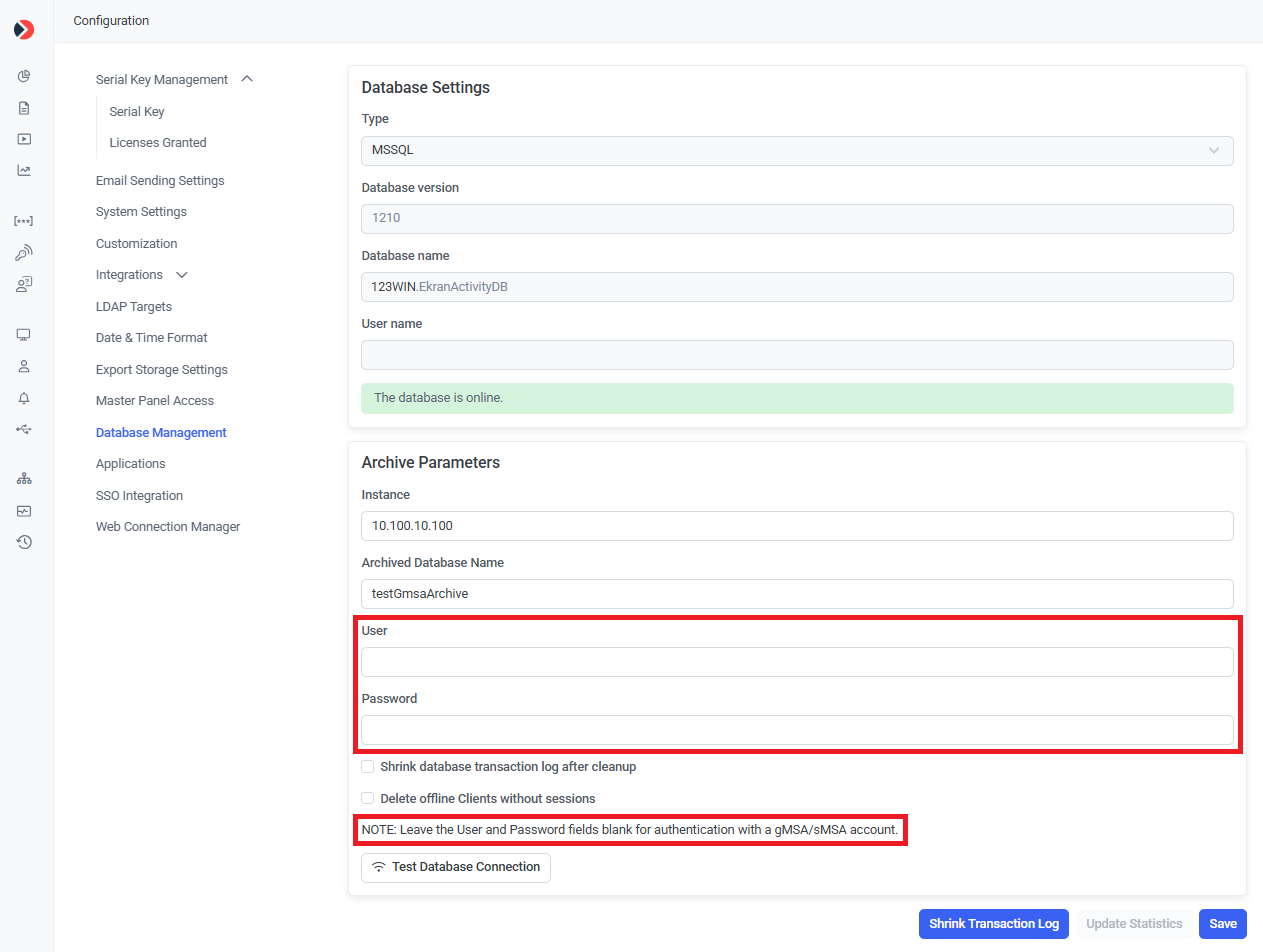
NOTE: Click the Test Database Connection button (at the bottom) to check whether the connection between the Application Server and the archived database is established.
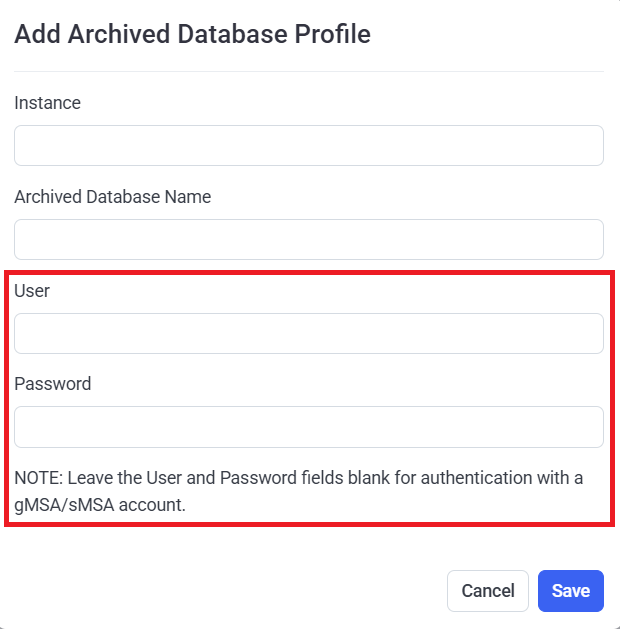
- Adding an archived database profile:
3. Troubleshooting
Issue 1: EkranServer does not run under the gMSA account.
a) Check if the gMSA account was added correctly by running the following command in PowerShell:
Test-ADServiceAccount <your_gMSA_login> |
The expected result of the command is True, but if it is False, check that the gMSA account has can be accessed on this computer, by running the following command:
Install-ADServiceAccount -Identity <your_gMSA_login> |
b) After creating the gMSA account, reboot the computer with the domain controller.
c) Check if there permissions are granted to Log on as a Service. Open msc > Local Policies > User Rights Assignment > Log on as a service.
d) Export EkranMasterCertificate.
e) Open the Microsoft Management Console (mmc) under the gMSA account, by using the following command:
.\PsExec64.exe -i -u <your_gMSA_login> mmc For example: .\PsExec64.exe -i -u "my.test\MyGmsa" mmc |
NOTE: PsExec is part of the PsTools suite, which can be download at: https://learn.microsoft.com/en-us/sysinternals/downloads/psexec
f) Import EkranMasterCertificate to Personal and Trusted Root Certification Authorities.
Issue 2: When the “Use process credentials” checkbox is selected, the connection to the database is lost, and the EkranServer service does not start.
a) It is worth checking which SPNs are registered for gMSA and whether MSSQLSvc\<SQLServerFQDN> is among them. Microsoft Kerberos Configuration Manager for SQL Server (https://techcommunity.microsoft.com/blog/sqlserver/released-microsoft-kerberos-configuration-manager-for-sql-server-v3-1/385138) can be used, which is a utility, where not only the correctness of the registered SPNs can be checked, but they can also be fixed in a few clicks.
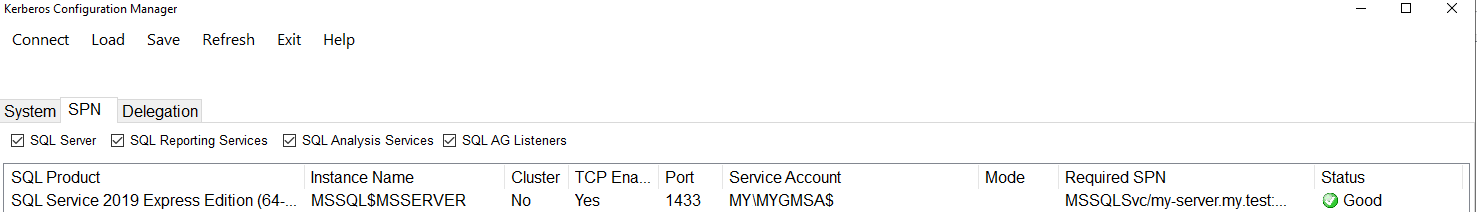
If it is not possible to install the utility, this can alternatively be done manually by running the following commands:
setspn -S MSSQLSvc/<SQLServerFQDN> <your_gMSA_login> For example: setspn -S MSSQLSvc/my-server.my.test:MSSERVER my\MyGmsa setspn -S MSSQLSvc/my-server.my.test:1433 my\MyGmsa |
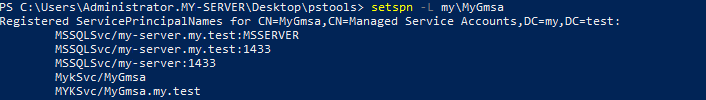
b) Check the SPNs added, by running the following command:
setspn -L <your_gMSA_login> |
c) Grant the Read and Write permissions for the SPN.
d) Enable Advanced Features in the Active Directory Users and Computers window, and open the properties on the computer which EkranServer service will run on (i.e. on which Syteca Application Server is installed), and on the Security tab, add permissions for the gMSA account (or the Active Directory group which the gMSA account will be used on) called Validated write to service principal name, and tenable the Read servicePrincipalName and Write servicePrincipalName properties:
e) For the group (when creating the gMSA account was specified as PrincipalsAllowedToRetrieveManagedPassword) that the gMSA account will be used on the computers in, add the Read and Write permissions for the SELF account (in a similar way as above).
The SQL Server logs will then be displayed as follows:

f) If the "18456, Severity: 14, State: 38 crashes" error occurs in the SQL Server logs, log in to SSMS under the "sa" account, and in the SQL server properties, on the Permissions page, add the Control server permission for the gMSA account.
