Remote Password (and SSH Key) Rotation
The Remote Password Rotation functionality allows the password (or SSH key) of the corresponding privileged user account to be changed automatically (to a new randomly-generated password) at a specified frequency, as well as manually at any time.
Remote password rotation can only be enabled for the Active Directory account, Windows account, Unix account (SSH), and MS SQL account secret types, and by a user with the Owner or Editor Role Type permissions for the secret.
SSH keys can also be rotated for the Unix account (SSH) secret type.
To configure remote password (and SSH Key) rotation for the account that users will access by using a secret in Syteca Connection Manager, do the following:
1. Log in to the Management Tool, and click the Password Management navigation link (on the left).
2. On the Password Management page, click anywhere on the required Active Directory account, Windows account, Unix account (SSH), or MS SQL account secret to edit it.
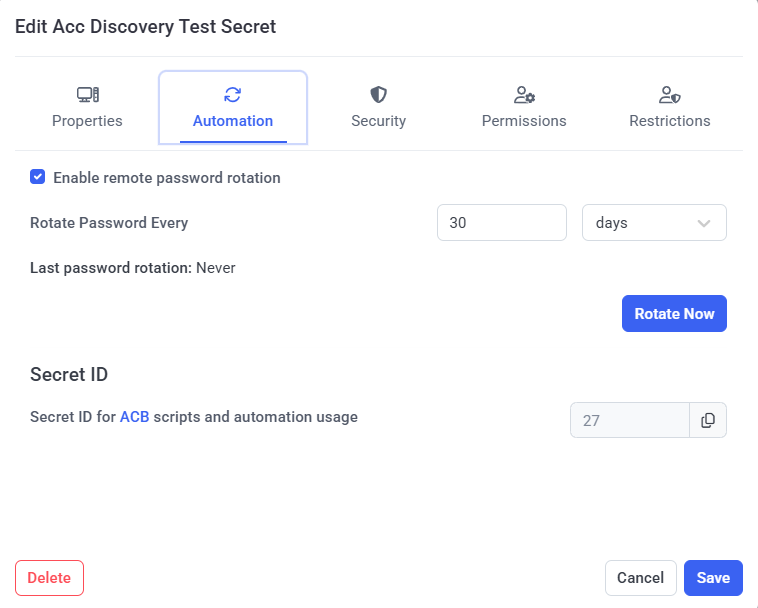
3. In the Edit Secret pop-up window that opens, select the Automation tab.
4. On the Automation tab, select the Enable remote password rotation checkbox, and specify how frequently the account's password will be rotated automatically (in the Rotate Password Every fields), or click the Rotate Now button to rotate the password immediately.
If remote password rotation ever fails, the "Failed" status is displayed in the (non-default) Password Rotation Status column on the Password Management page, as well as the corresponding error event on the System Health page. In this case, subsequent password rotation will no longer occur.
For remote password rotation to function correctly for the accounts (that the secrets access), both:
• It needs to be configured appropriately on the corresponding hosts (including to ensure that the policies do not conflict with remote password rotation).
• The required preconditions need to be met (as described below).
Table of Contents
1. Preconditions for Windows Account Secrets
The following preconditions need to be met on the remote computer where the Windows account is located (i.e. on the target computer that the secret connects to by using Syteca Connection Manager):
1. Remote UAC must be disabled (on computers running the Windows 11 and Windows 10 desktop operating systems), by doing the following:
a) Open the Windows Registry Editor.
b) Locate and select the following key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System.
c) If the LocalAccountTokenFilterPolicy registry entry does not exist, select Edit > New > DWORD (32-bit) Value, and add the following new values in the fields:
• Value name: LocalAccountTokenFilterPolicy
• Value data: 1
d) If a LocalAccountTokenFilterPolicy registry entry already exists, right-click it and select Modify in the context menu, then enter “1” in the Value data field, and click OK.
e) Restart the computer.
2. The Remote Registry service must be running (including on computers running the Windows 11 and Windows 10 desktop operating systems).
On some OSs, the Remote Registry service can stop automatically (which causes password rotation to fail) after initially running (e.g. after 10 minutes), so admins need to monitor its state.
To prevent the Remote Registry service from automatically stopping, set the following Windows registry key to:
• Key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\RemoteRegistry
• Name: DisableIdleStop
• REG_DWORD, data: 1
3. Make sure the local security policy is configured correctly (so that the account will never be locked out), by doing the following:
a) Press Win+R, then enter secpol.msc, and click Enter.
b) In the Local Security Policy window that opens, select the Security Settings section (on the left).
c) Open Account Policies, and select Account Lockout Policy.
d) Double-click on the Account lockout threshold policy (on the right) to open the settings Account lockout threshold Properties window.
e) Make sure that the value specified in the Account will lock out after field is “0” to disable account lockout, and click Apply and then OK to save any changes made.
4. Make sure the password settings for the account are configured to never expire, by doing the following:
a) Press Win+R, then enter lusrmgr.msc, and click Enter.
b) In the Local Users and Groups (Local) section, select the Users section.
c) Right-click on the user required, and select Properties.
d) On the General tab, make sure that the Password never expires checkbox is selected, and then click OK.
5. In the firewall, the following rules must be enabled:
• Remote Service Management (NP-ln).
• Remote Service Management (RPC).
6. Make sure the "Minimum password age" is set to "0" days in the Password Policy (so that remote password rotation will not fail), by doing the following:
a) In Local Security Policy, open the Security Settings > Account Policies > Password Policy folder.
b) Set the "Minimum password age" to "0" days.
The Syteca Application Server host must also be able to resolve the hostnames of the target computers during account onboarding of computers (please also refer to the Account Discovery page), as follows:
If a Windows local account is being onboarded using the hostname of the computer where it was found, the host where Syteca Application Server is running must be able to resolve that hostname. This is important in case a target computer belongs to a domain other than the host of Syteca Application Server.
For the Syteca Application Server host to be able to resolve the hostnames of the target computers, do the following:
• For example, as a possible solution, the Syteca Application Server host can have a domain suffix search list configured which all available domains in the network are included in.
NOTE: For more information, please refer to: https://learn.microsoft.com/en-us/troubleshoot/windows-client/networking/configure-domain-suffix-search-list-domain-name-system-clients
NOTE: As an alternative to domain suffix search list configuration, consider using FQDN or IP addresses of the target computers during onboarding.
NOTE: Remote Password Rotation is only available for local administrator accounts.
NOTE: The EkranServer service must be run under any user account except the LocalSystem account (on the computer where Syteca Application Server is installed).
2. Preconditions for Unix Account (SSH) Secrets (for Password Rotation, SSH Key Rotation, and Linux Account Discovery)
NOTE: For the Unix account (SSH) secret type, PuTTY needs to be installed on the computer with Syteca Connection Manager for the secret to function correctly, and the "Use SSH key" option can also be selected (instead of the "Use password" option) when adding the secret.
Syteca allows the passwords and SSH keys of Unix account (SSH) secrets to be rotated, which means that they are changed automatically (to a new randomly-generated ones) on a regular basis to reduce the risk of them being compromised.
The Unix account (SSH) secret type has two account options for connection:
• Using a password
• Using an SSH key
Accordingly, rotation of SSH passwords and SSH keys work in different ways.
NOTE: In most cases, the target host defined in the secret will use an OpenSSH server that is commonly used in most Linux systems. For this reason, for the purposes of this document it is assumed that an OpenSSH server is used. For correct usage and password/key rotation of Unix account (SSH) secrets, the target host defined in the Unix account (SSH) secret should first of all be correctly configured and running the OpenSSH server.
2.1. Preconditions for SSH Password Rotation for Unix Account (SSH) Secrets
Preconditions: The user Login and Password defined in the Unix account (SSH) secret should be valid for the target host.
Rotation logic: The Syteca Application Server connects to the target host using the credentials defined in the secret, and changes the password of the current user to a new one generated.
Both the old and new passwords are stored in the Application Server database during all operations, and the old password is only deleted from the database after all operations have completed successfully.
In the case of failure, the secret's password is restored to a valid state using one of the two passwords.
2.2. Preconditions for SSH Key Rotation for Unix Account (SSH) Secrets
Preconditions: The user Login and Private Key (and the Private Key Passphrase) defined in the Unix account (SSH) secret must be valid for the target host, and the corresponding public key needs to be located in the ~/.ssh/authorized_keys file (in the user's home directory on the target host).
As an SSH client, the PuTTY application can be used, and should be installed on the computer with Syteca Connection Manager (although this is not required for rotation, the SSH key used in the secret should be in the PuTTY format). For PuTTY key generation, and for OpenSSH server configuration using PuTTY, see: https://www.ssh.com/academy/ssh/putty/windows/puttygen.
Rotation logic: The Syteca Application Server connects to the target host using the Login and Private Key defined in the secret, and replaces the public key defined in the ~/.ssh/authorized_keys file with the new one that corresponds to the new PuTTY key generated.
Both the old and new keys (and their passphrases) are stored in the Application Server database during all operations, and the old key is only deleted from the database after all operations have completed successfully.
In the case of failure, the secret key (and passphrase) are restored to a valid state using one of the two keys.
If the connection via a Unix account (SSH) secret to the remote Linux computer using an SSH key is successful, but the password rotation for this secret fails (with the following error added to the System Health Transaction log: "Password rotation for Secret SSH failed. Error: Permission denied (publickey)"), then "PubkeyAcceptedKeyTypes +ssh-rsa" needs to be added to the /etc/ssh/sshd_config file, as follows.
• In the /etc/ssh directory, open the ./sshd_config file (which is read-only) in an editor to be able to make changes.
• Add "PubkeyAcceptedKeyTypes +ssh-rsa" to the file, and save the changes.
• Run the following command: sudo systemctl restart sshd
2.3. NOT AVAILABLE IN SAAS Preconditions for Establishing SSH Connections (for Password Rotation, SSH Key Rotation, and Linux Account Discovery)
Check the following to ensure that an SSH connection is established to the target computer:
1. Make sure that the target computer is online.
2. Make sure that the OpenSSH server is installed and running, by running the following command:
sudo systemctl status ssh
Otherwise, do as follows:
a) Install OpenSSH Server on the target computer, by running the following commands:
sudo apt update
sudo apt install openssh-server
b) Start and enable the SSH service, by running the following commands:
sudo systemctl start ssh
sudo systemctl enable ssh
c) Check the SSH service status again (see above).
3. If a firewall is installed, allow the SSH connection in it, as follows:
a) For Ubuntu/Debian, by running the following commands:
sudo ufw allow ssh
sudo ufw enable
b) For CentOS/RHEL, by running the following commands:
sudo firewall-cmd --permanent --add-service=ssh
sudo firewall-cmd --reload
4. Make sure that the default SSH port is allowed by the firewall (if a firewall is enabled), as follows:
a) For Ubuntu/Debian, by running the following commands:
sudo ufw allow 22/tcp
sudo ufw reload
b) For CentOS/RHEL, by running the following commands:
sudo firewall-cmd --permanent --add-port=22/tcp
sudo firewall-cmd --reload
5. Check that the sshd configuration file is valid, by running the following command:
sudo sshd -t
NOTE: If there is no output, then the configuration file is valid.
6. Check the ssh configuration on the computer that Syteca Application Server is installed on:
a) Open the command prompt (e.g. by pressing WIN+R , and entering “cmd”).
b) In the command prompt, try to connect to the target computer via ssh, by running the following command:
ssh {user name}@{targetComputer ip or hostname} -p 22
c) Add the hostname to the target hosts if prompted to (which does not affect scanning or onboarding).
d) If the connection is successful, then the SSH connection is established.
