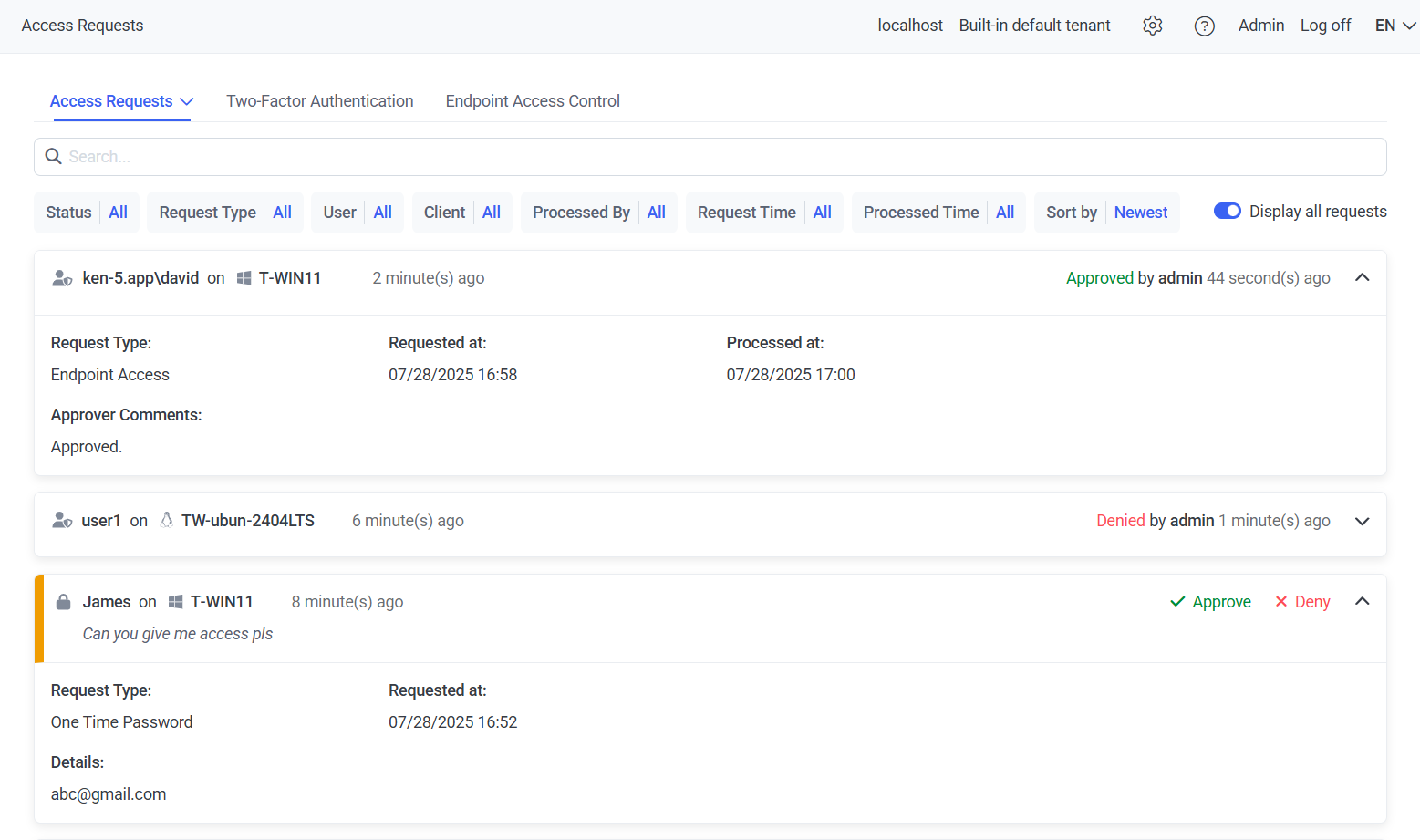
Managing Access Requests
On the Access Requests tab (on the Access Requests page), the following types of user access requests are displayed:
• Endpoint Access requests (see the Endpoint Access Control section).
• One-Time Password requests (see the Requesting a One-Time Password and Logging In page).
• Access to Usage of Secret requests (see the Using Secrets page).
• Mass Storage Device Access requests (see the Requesting Access to a Blocked USB Device page).
• Expose requests (see the Pseudonymizer page).
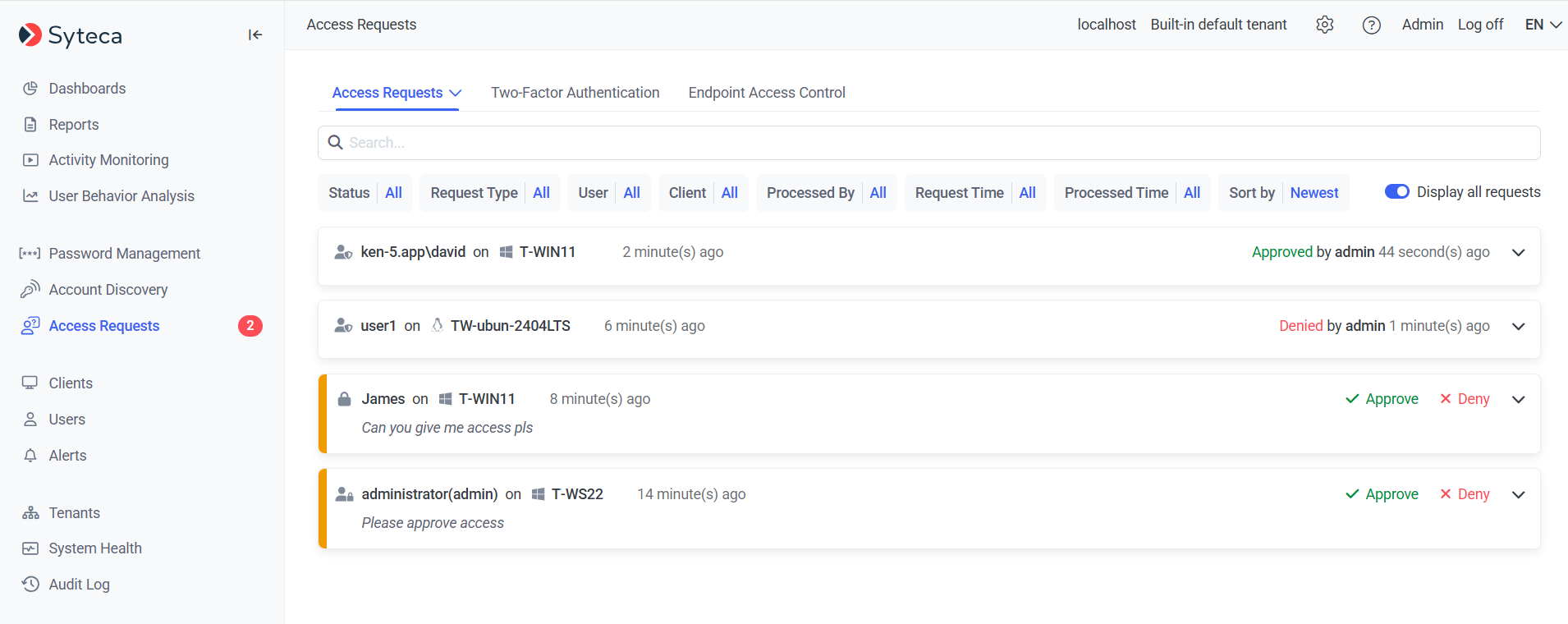
The number of pending access requests is displayed in the red circle (
The Display all requests toggle switch slider (in the top right) can be used to also view all old requests i.e. requests that are no longer pending (including Approved, Denied, and Expired requests).
By default, if any request is not processed within 30 minutes after it has been submitted, it will automatically expire. This setting can be changed (in the Access Request Expiration Time section) on the System Settings tab, on the Configuration page.
NOTE: A user can only see access requests for which they have been listed as an Approver.
The Approver can process a request by clicking the Approve or Deny buttons (on the right of each request), and in the popup window that opens, and optionally enter a text message, and then click Confirm.
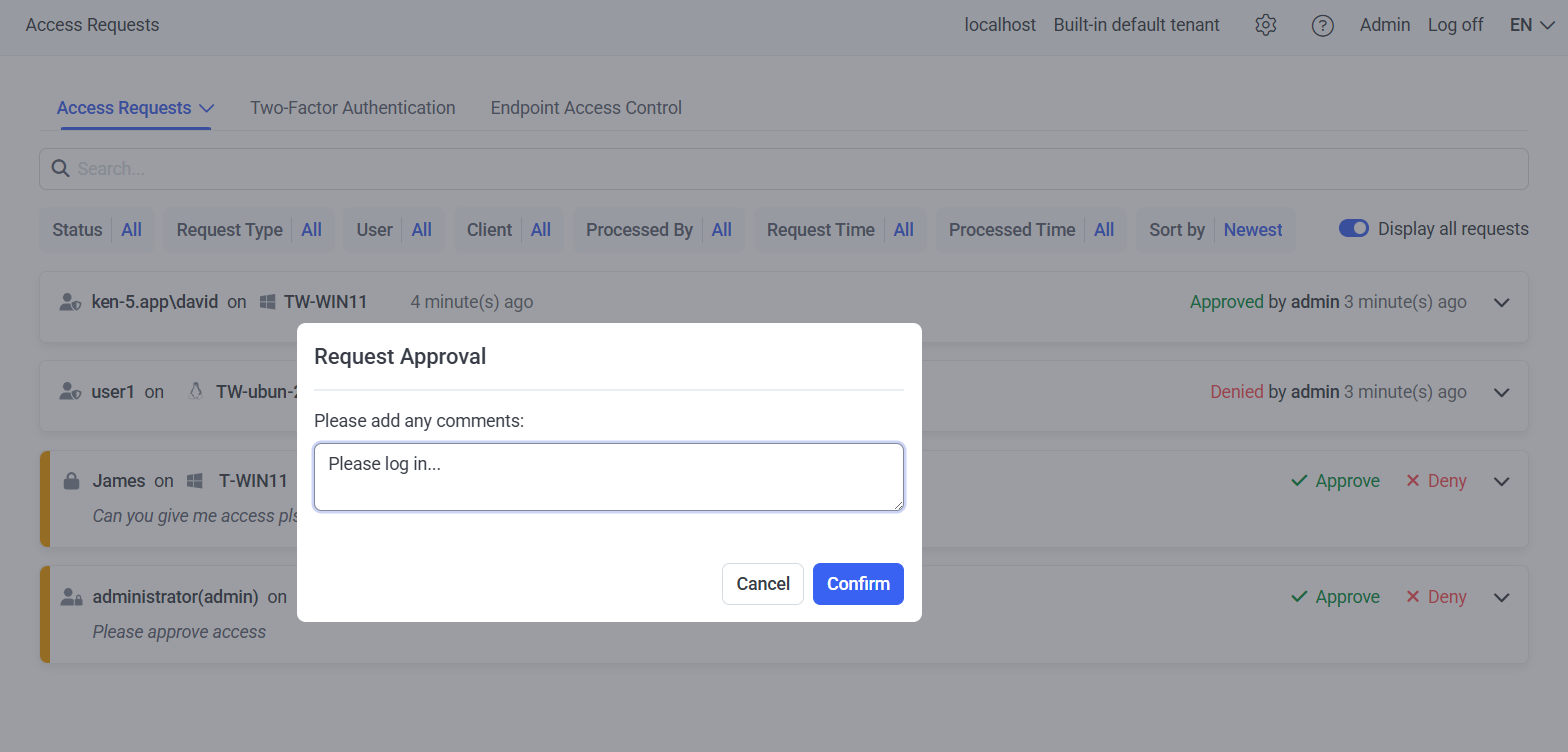
NOTE: If the Pseudonymizer feature is enabled, and a de-anonymization password is enabled, then the de-anonymization password also needs to be entered in to the additional “Please enter the de-anonymization password” field which is displayed in this pop-up window.
To view detailed information about an access request, click the