Two-Factor Authentication
Two-factor authentication (2FA) allows you to provide an extra layer of protection, by requiring users of critical endpoints in the network to additionally enter a time-based one-time password (TOTP) generated by using a mobile application to log in.
This Syteca feature is available for Windows Client computers (for local and Active Directory users) and Linux Client computers (for local users only), and supports Google Authenticator and Microsoft Authenticator (and other third-party authenticator applications), which can be installed on a mobile device or a computer.
Both Linux terminal (local and SSH) and GUI sessions (including when using Wayland) are supported.
To require endpoint users to log in to Client computers using 2FA, this feature first needs to be configured for both:
• [Required for users of Linux Client computers only:] Users (by adding each one manually using the Add button on the Two-factor Authentication tab, on the Access Requests page).
NOTE: Users of Windows Client computers also need to be added manually only in the (unlikely) event that the Mass 2FA feature is disabled (i.e. the “Do not generate QR code automatically" checkbox is selected on the Authentication Options tab while editing the Client / Client group).
• [Required for both the Windows and Linux Client computers of the users:] Client computers (by selecting the Enable two-factor authentication checkbox while editing a Client / Client group, on the Clients page).
NOTE: The additional Mass 2FA feature now allows automatic configuration of 2FA for all users of an individual Windows Client computer (or all the Windows Client computers in a Client group), but not currently for Linux Client computers. This means that after enabling 2FA on Windows Clients, Windows users are automatically added to the grid on the Two-Factor Authentication tab on the Access Requests page (i.e. by the users themselves on their next login, when they scan the QR code displayed), and so no longer need to be added manually.
To configure 2FA, follow the instructions described in the steps below.
Table of Contents
1. Configuring 2FA for Users Manually
[Required for users of Linux Client computers only:] 2FA needs to be configured manually for each user (or user group) individually (by adding them on the Access Requests page).
NOTE: This step is also required for users of Windows Client computers only in the (unlikely) event that the Mass 2FA feature is disabled (i.e. the “Do not generate QR code automatically" checkbox is selected on the Authentication Options tab while editing the Client / Client group), since these Windows users will otherwise be configured automatically when they scan a QR code which is displayed on the screen on their first login after 2FA has been enabled on their Client computer/s (see below).
To configure two-factor authentication for a Linux (or, if required, Windows) user manually, do the following:
1. Log into the Management Tool as a user with the administrative User Management permission.
2. Open the Access Requests page, and select the Two-Factor Authentication tab, and then click the Add button (in the top right of the page).
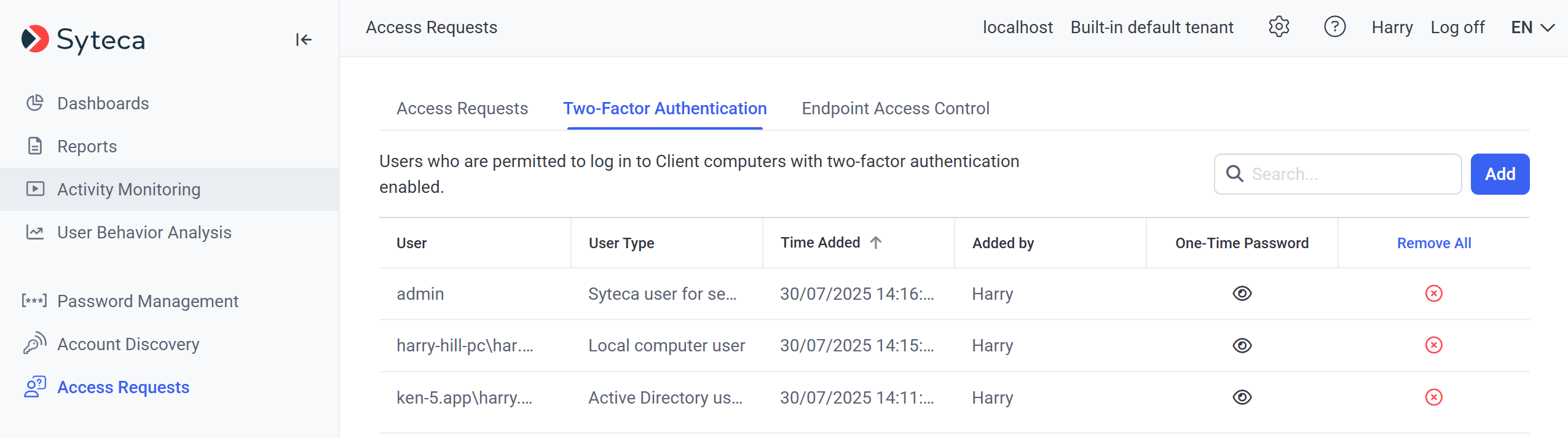
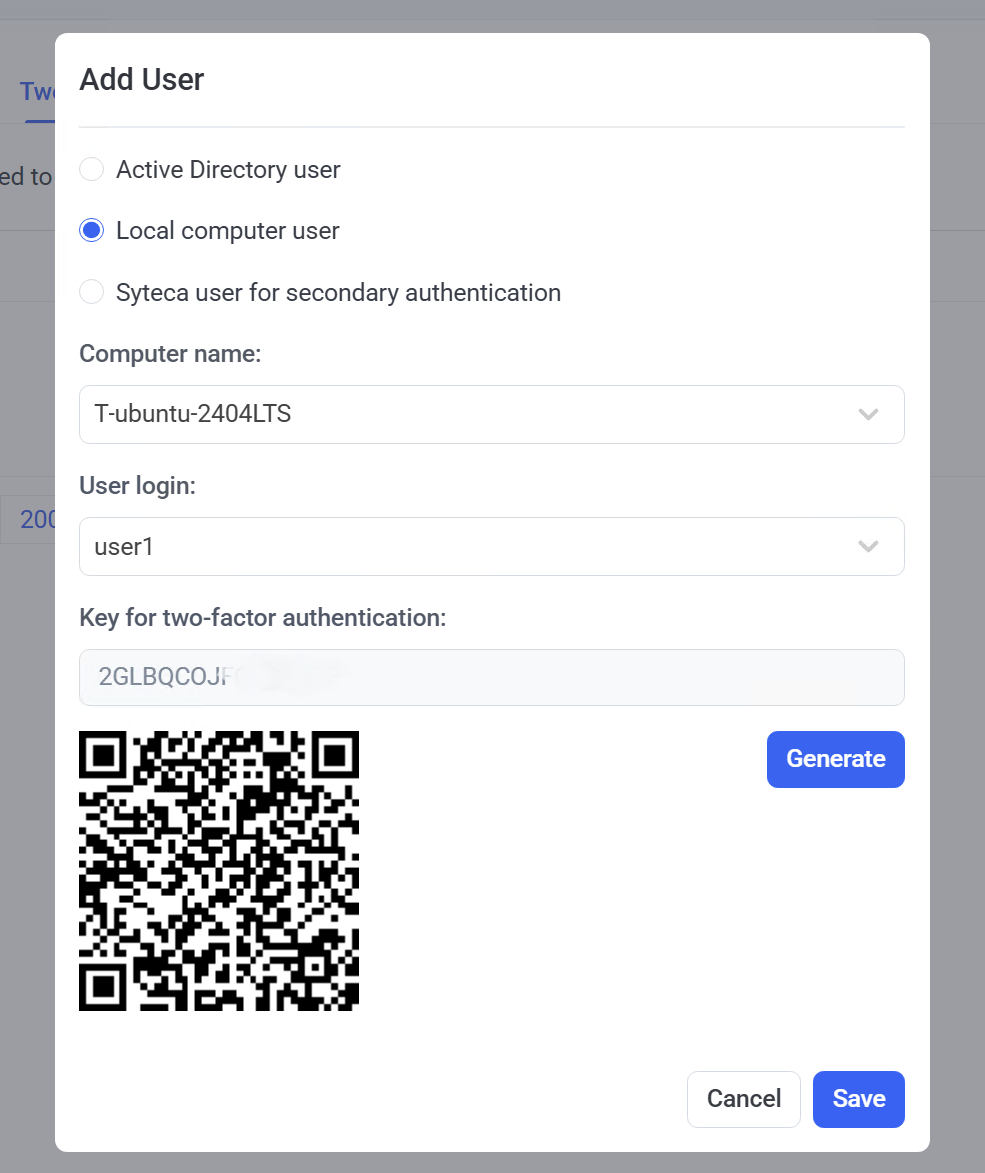
3. Select and configure one of the following options for the user in the Add User pop-up window that opens:
• [For Windows Clients only:] Active Directory user: Select this option for a domain user, and then select the Domain and the User login name required.
NOTE: Currently, only individual users can be added, but not user groups.
• [For Windows and Linux Clients:] Local computer user: Select this option for a local user, and then select the local Computer name and the User login name required.
NOTE: On Linux Client computers, only the “Local computer user” type is currently supported for 2FA.
• [For Windows Clients only:] Syteca user for secondary authentication: Select this option for a user that has been added to Syteca Management Tool to use for secondary authentication, and then select the User login name required.

4. Click the Generate button to create a QR code (and a key displayed above it) for 2FA user access, and then copy the QR code (and the key), to send it to the corresponding user.
NOTE: After closing the pop-up window, it will not be possible for any user to view the QR code (or key) again for security reasons.
5. Click the Save button, and the user is then added to the list of users displayed in the grid on the Two-Factor Authentication tab (on the Access Requests page).
NOTE: As soon as a user is added, if 2FA is also enabled on a Client computer they use (see below), then when the user first logs in, they will be required to scan the QR code (provided to them by the Management Tool user who added them above) using an authenticator app (e.g. Google Authenticator or Microsoft Authenticator), and thereafter use the app to generate a 2FA time-based one-time-password (TOTP) each time they log in.
2. Enabling 2FA on Client Computers
[Required for all Windows and Linux Client computers:] 2FA needs to be enabled on Client computers to require users to log in to them using 2FA.
To enable two-factor authentication on a Client computer (or all the Windows and Linux computers in a Client group), do the following:
1. Log in to the Management Tool as a user with the Client Configuration Management permission for Clients.
2. Open the Clients page, find the required Client / Client group, and click on its name to edit it.
3. Select the Authentication Options tab, and scroll down to the Two-Factor and Secondary Authentication section.
4. Select the Enable two-factor authentication checkbox to enable this option.
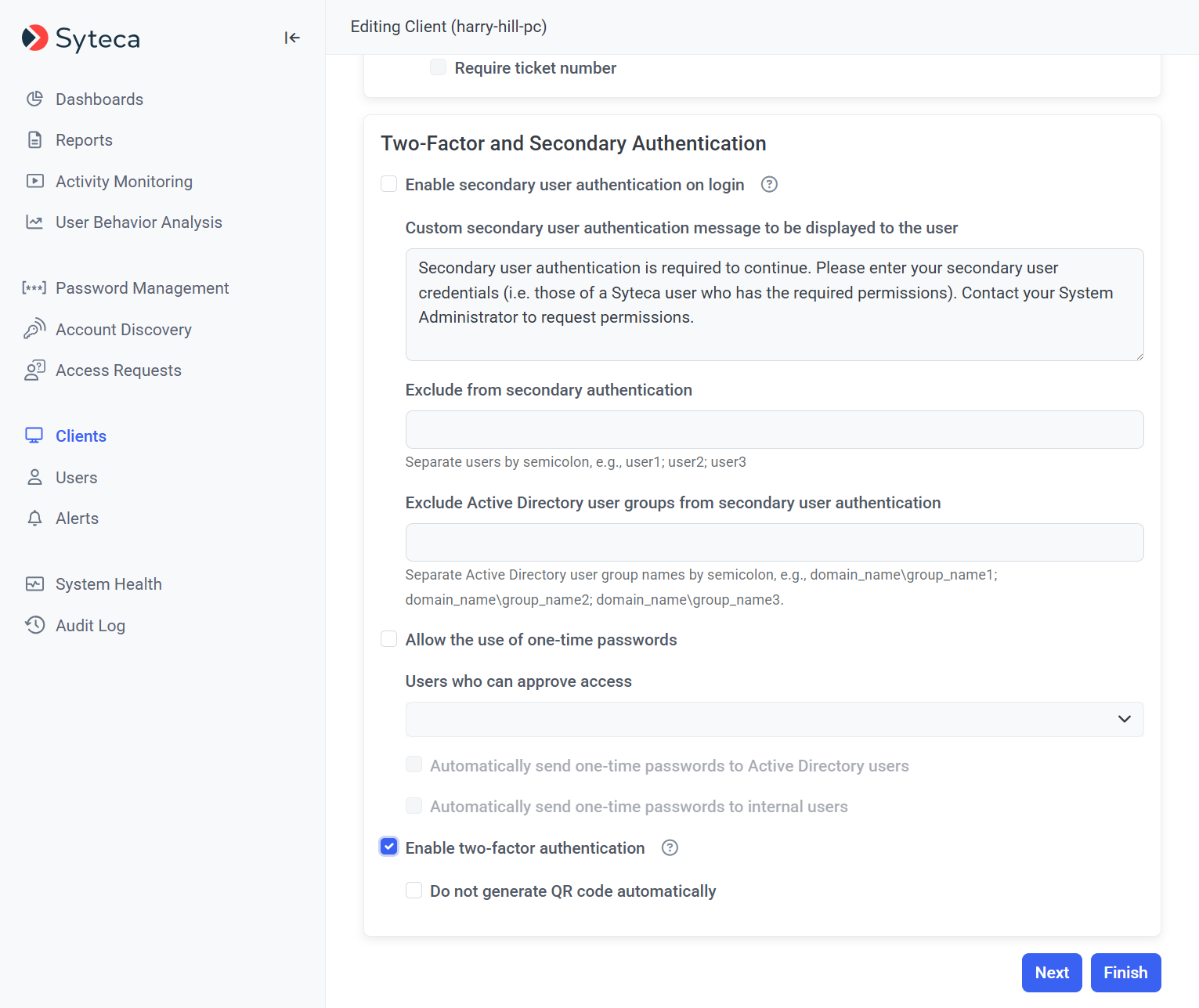
NOTE: After 2FA has been enabled for the Client (or Client group), on their first login all users of the corresponding Client computer(s) will be required to scan a QR code with their authenticator app (e.g. Google Authenticator or Microsoft Authenticator), and thereafter use the app to generate a 2FA one-time password (TOTP) each time they log in.
5. [For Windows users only:] Also select the Do not generate QR code automatically checkbox in the (unlikely) event that you want to disable the Mass 2FA feature, so that all users of the Windows Client computer(s) (who will be required to use 2FA to log in) instead need to be first added manually on the Access Requests page).
6. Click the Finish button (at the bottom of the page) to apply the changes.
3. Logging into a Client Computer Using 2FA
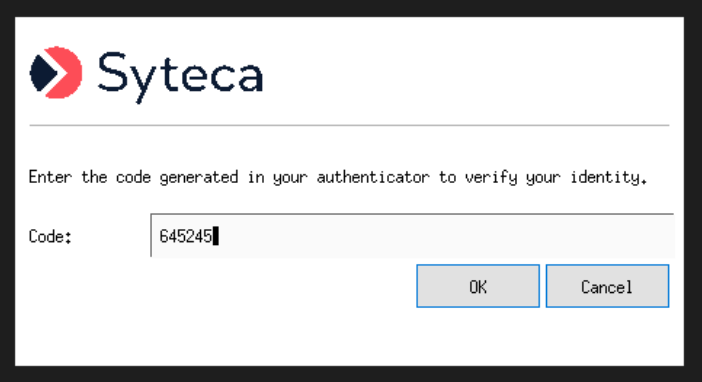
A user of a Client computer needs to log in under their Windows / Linux / Active Directory credentials, and Syteca will then prompt them to enter a 2FA time-based one-time password (TOTP) generated using their authenticator app (e.g. Google Authenticator or Microsoft Authenticator).
NOTE: On their first login, after 2FA has been enabled for the Client (or Client group), any user of the Client computer/s concerned will be required to scan a QR code with (or enter a key into) their authenticator app (e.g. Google Authenticator or Microsoft Authenticator), and thereafter use the app to generate a 2FA time-based one-time password (TOTP) each time they log in:
• Where a 2FA user has been configured manually (see above - only usually for Linux users, but may also be for Windows users), the QR code (or the key displayed above it) needs to be provided to the user by the Management Tool user who added them.
• Where a 2FA user has not been configured manually (see above - only for Windows users), the QR code (and the key displayed below it) will be displayed on a user's first login after 2FA has been enabled for their Client computer.

NOTE: After selecting the "I have saved the code to my authenticator device" checkbox, and clicking Confirm, the user is added to the list of users displayed in the grid on the Two-Factor Authentication tab (on the Access Requests page).
NOTE: The text displayed (on the left of the QR code) can be customized in the Management Tool on the Configuration page (on the Customization tab, scroll down to the Two-Factor Authentication section).
After entering the one-time password generated by their authenticator app, and then clicking OK, the user will then be logged into the Client computer (and be automatically added to the list of users displayed on the Two-Factor Authentication tab on the Access Requests page).
NOTE: If a user cannot generate a 2FA one-time password (TOTP) themselves (any time after they have initially scanned the QR code), they can instead contact a Management Tool user to request that the current one-time password (which changes every 30 seconds) be provided to them.
NOTE: For a user to be authenticated using 2FA, the system time and the time zone on the Syteca Application Server computer and on the user's device must be synchronized.
4. Managing 2FA Access for Users
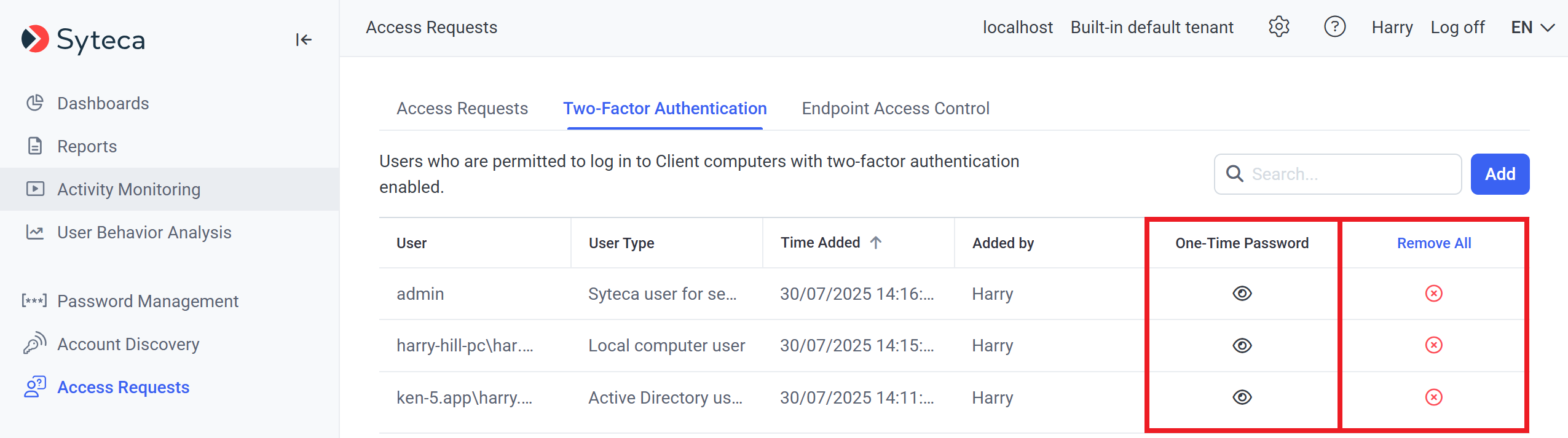
The list of users with 2FA configured is displayed in the grid on the Two-Factor Authentication tab (on the Access Requests page), where their 2FA access can be managed by a Management Tool user with the Client Configuration Management permission for Clients and administrative User Management permission as follows:
• Click the Show (
• Click the Remove (
NOTE: So that the user is no longer required to (scan a QR code or) enter a 2FA one-time password on login, 2FA also needs to be disabled on the user's Client computer/s (by deselecting the "Enable two-factor authentication" checkbox while editing the corresponding Client(s) / Client group(s) on the Clients page.
NOTE: If the corresponding Client computer is offline when any user is deleted from the grid, the "Enable two-factor authentication" checkbox (while editing the Client / Client group on the Clients page) first needs to be deselected and then selected again, before the user will be able to log in using 2FA again.
• [For Linux users only:] Click the Add button (as described above) to manually add individual users (or user groups) who will be required to use 2FA to log in (and will need to be sent the QR code manually).
NOTE: Adding individual users (who will be required to use 2FA to log in) manually is only usually required for Linux users, as they are not currently supported by the additional Mass 2FA feature. However, Windows users also need to be added manually only in the (unlikely) event that the Mass 2FA feature is disabled (i.e. if the “Do not generate QR code automatically” checkbox is selected on the Authentication Options tab while editing the Client / Client group).