Moving the Master Certificate to Thales HSM External Storage
NOT AVAILABLE IN SAAS
To enhance security, the Syteca Master Certificate (EkranMasterCertificate) can be moved to a Thales HSM (hardware security module) external storage device by using Thales SafeNet KeySecure with SafeNet ProtectApp.
Table of Contents
1. Preconditions
The following applications first need to be installed and configured:
• The SafeNet KeySecure keystore application needs to be installed on any machine, and a user account set up in its SafeNet KeySecure (keystore) Management Console. Please consult the SafeNet KeySecure technical documentation for detailed information.
• The SafeNet ProtectApp for .NET SDK needs to be installed on the machine where Syteca Application Server is installed, and configured as described below. Please consult the SafeNet ProtectApp for .NET technical documentation for detailed information.
NOTE: For large deployments with multiple Syteca Application Server instances installed on different machines in a cluster, the SafeNet ProtectApp for .NET SDK needs to be installed and configured on each of them.
2. Integrating the Application Server with Thales HSM
Before the Master Certificate can be moved, the integration between the Application Server and the Thales HSM needs to be built. This is done by using the SafeNet ProtectApp for .NET SDK to define the parameters for the connection between the Application Server and the SafeNet KeySecure keystore NAE-XML server (and well as other optional parameters).
To build the integration, define the connection parameters by doing the following:
1. In the SafeNet ProtectApp for .NET SDK, locate and open the SafeNet ProtectAppForDotNet.properties file (further referred to as the .properties file).
2. Scroll down to the line containing just "NAE_IP=", and immediately after this text, add the IP address of the machine where the SafeNet KeySecure keystore application is installed.
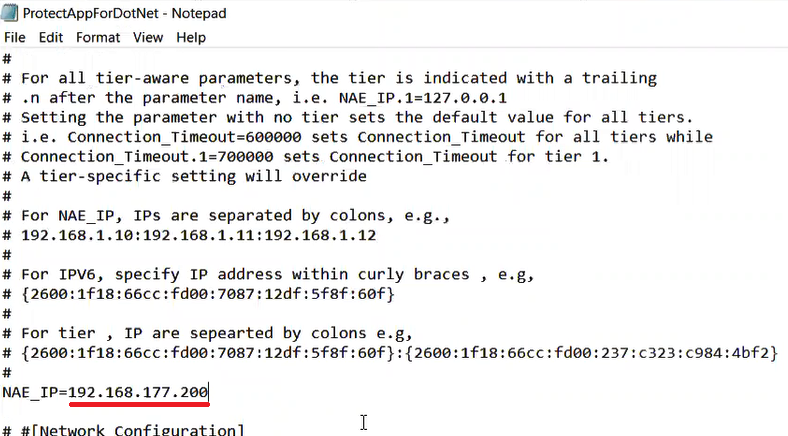
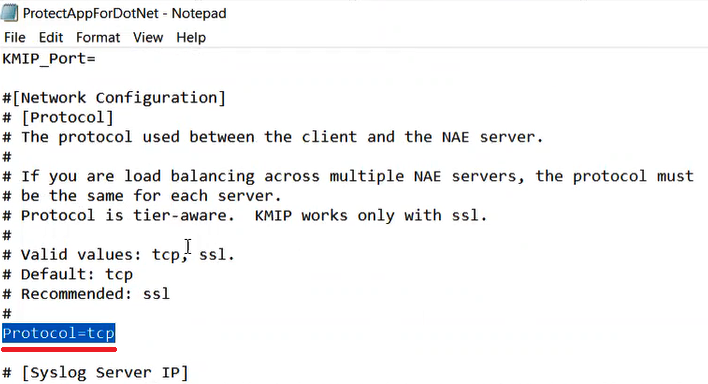
3. If Master Certificate SSL authentication is required, change "Protocol=tcp" to "Protocol=ssl" in the .properties file.
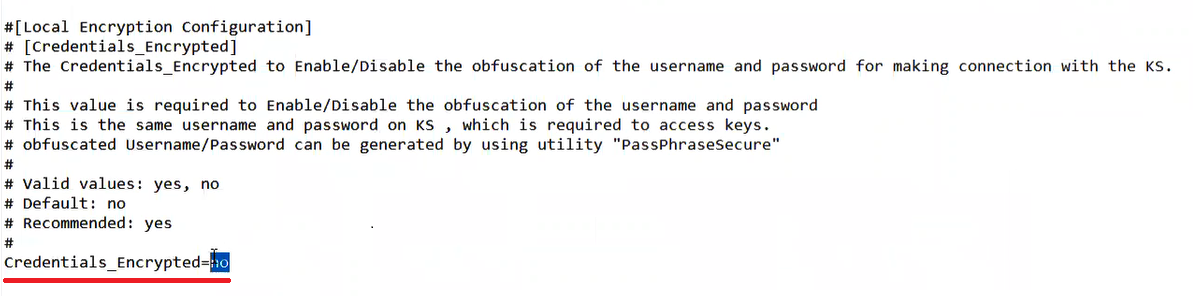
4. If the credentials need to be encrypted, change "Credentials_Encrypted=no" to "Credentials_Encrypted=yes" in the .properties file.
NOTE: Other options (e.g. load balancing) for the integration can also be configured. Please consult the SafeNet ProtectApp for .NET technical documentation for detailed information.
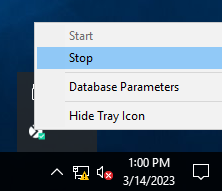
5. Restart Syteca Application Server (i.e. EkranServer service), which can be done by stopping and then starting the Application Server again, by right clicking on the Syteca Server tray icon in the Windows notification area.
3. Moving the Master Certificate to Thales HSM
After the Application Server has been integrated with Thales HSM by defining the connection parameters for the Application Server to access the SafeNet KeySecure NAE-XML server (as described above), the Master Certificate can now be moved to the HSM external storage.
To move the Master Certificate to Thales HSM external storage, do the following:
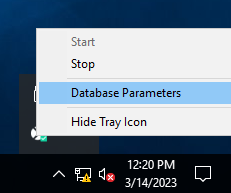
1. As a local user, right-click the Syteca Server tray icon in the Windows notification area, and select Database Parameters to open the Database Parameters (DbSetupToolUI) application pop-up window.
2. Select the Advanced tab, and then click the Switch Master Certificate to SafeNet KeySecure button.
.png?inst-v=8a279e6e-4708-44c0-8d8e-079ebd0a0acf)
4. In the SafeNet KeySecure Options pop-up window that opens, define the following values in the corresponding fields, and then click Next:
• SafeNet properties file location field: Specify the location of the .properties file.
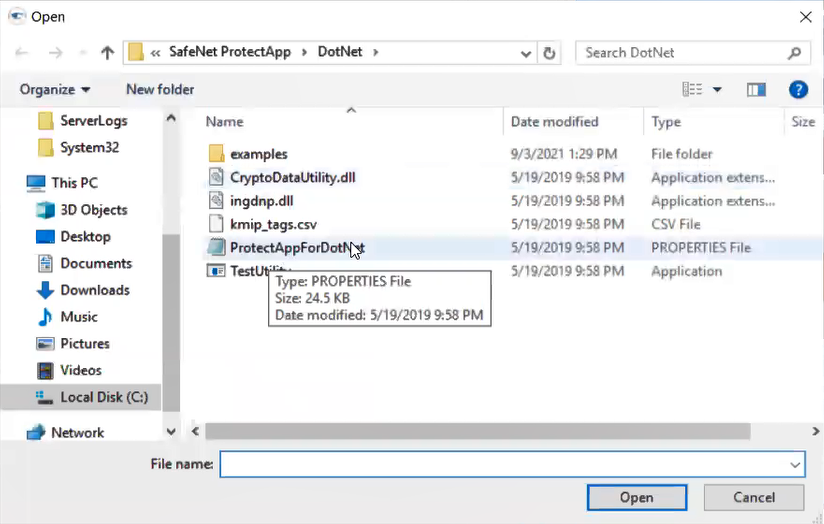
• PassPhraseSecure.exe location field: If the credentials are specified as encrypted in the .properties file, specify the location of the PassPhraseSecure.exe file
NOTE: This field will be disabled if the credentials are not specified as encrypted in the .properties file, as described above).
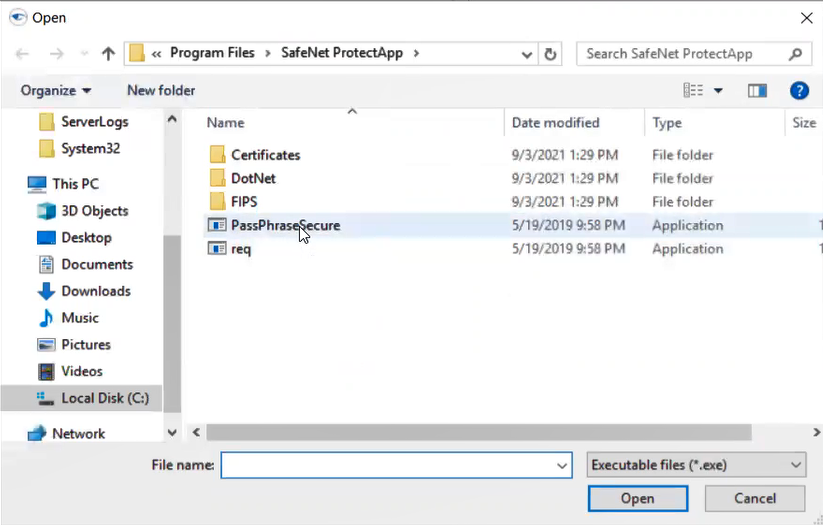
• User name field: Enter the login name of the SafeNet KeySecure (keystore) Management Console user.
• Password field: Enter the password of the SafeNet KeySecure (keystore) Management Console user.
• Key name field: Leave this field empty to generate a key (if no key yet exists, since this is the first time that a key is to be generated), or enter the name of an existing private key (if you have one) and then select the First node deployment option, and then click Next.
.png?inst-v=8a279e6e-4708-44c0-8d8e-079ebd0a0acf)
5. In the pop-up window that opens, click Yes to restart the Application Server and complete building the integration.
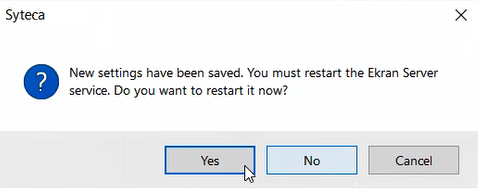
NOTE: After moving the Master Certificate to Thales HSM storage:
• The old Master Certificate (in the old storage location) can no longer be used, since a new key has now been generated for it (and the old Master Certificate can be deleted manually if required).
• The Master Certificate can no longer be reissued (by using the Reissue Master Certificate button on the Advanced tab of Database Parameters (DbSetupToolUI) application).
• If the Application Server is reinstalled, the Master Certificate will remain stored on the HSM and fully functional, and so will not need to be moved there again or reconfigured in any way.
4. Changing the Connection Parameters
The SafeNet KeySecure Options need to be updated whenever the .properties file is modified, or if the credentials of the user in the SafeNet KeySecure (keystore) Management Console have been changed.
To update the values of the SafeNet KeySecure Options, do the following:
1. Copy the existing key from the Key name field on the Advanced tab of the Database Parameters (DbSetupToolUI) application.
.png?inst-v=8a279e6e-4708-44c0-8d8e-079ebd0a0acf)
2. Click the Switch Master Certificate to SafeNet KeySecure button.
3. In the SafeNet KeySecure Options pop-up window that opens, change the appropriate values.
4. Paste the existing key (copied above) into the Key name field, and then select the First node deployment option.
NOTE: The Key cannot be rotated (by leaving the Key name field empty) while updating the SafeNet KeySecure Options.
.png?inst-v=8a279e6e-4708-44c0-8d8e-079ebd0a0acf)
5. Click Next, and in the pop-up window that opens, click Yes to restart the Application Server and complete updating the SafeNet KeySecure Options.
5. Rotating the Key
Whenever the key needs to be changed, a new one can be generated simply by clicking the Switch Master Certificate to SafeNet KeySecure button once again, and making sure that no key is specified in the Key name field (in the SafeNet KeySecure Options pop up window that opens) and then clicking Next, and restarting the Application Server.
If you want to use an existing key (if you have one), enter the name of the key in the Key name field, and select the First node deployment option.
NOTE: While doing this, the other values in the SafeNet KeySecure Options pop-up window must not be modified.
6. Large Deployments with Multiple Application Server Instances
For large deployments with multiple Application Servers instances in a cluster, the process is the same as described above, but for each additional Application Server, the key needs to be copied from the Key name field (on the Advanced tab of the Database Parameters (DbSetupToolUI) application) on the node with the first instance of the Application Server, and pasted into the Key name field in the SafeNet KeySecure Options pop up window on the additional Application Server node (instead of leaving this field empty), and the Subsequent node deployment option then needs to be selected.
After completing configuration on each additional Application Server node, the Database Parameters (DbSetupToolUI) application on it should be closed and then relaunched, and the database parameters (on the Parameters tab) specified once again (if they are not displayed).
NOTE: Whenever the Switch Master Certificate to SafeNet KeySecure button is used again (e.g. either to update the SafeNet KeySecure Options or to rotate the key) on any Application Server instance, each additional Application Server node will again need to be configured manually in the same way as described in this section.

.png?inst-v=8a279e6e-4708-44c0-8d8e-079ebd0a0acf)